Website Security
How to Improve Your Websites Safety
1.Keep Software And Plugins Up-To-Date
Every day, there are countless websites compromised due to outdated
software. Potential hackers and bots are scanning sites to attack.
Updates are vital to the health and security of your website. If your site’s
software or applications are not up-to-date, your site is not secure.
Take all software and plugin update requests seriously.
Updates often contain security enhancements and vulnerability repairs. Check
your website for updates or add an update notification plugin. Some platforms
allow automatic updates, which is another option to ensure website security.
The longer you wait, the less secure your site will be. Make updating your
website and its components a top priority.
2.Add HTTPS and an SSL Certificate
To keep your website safe, you need a secure URL. If your site visitors offer
to send their private information, you need HTTPS, not HTTP, to deliver it.
What is HTTPs?
HTTPS (Hypertext Transfer Protocol Secure) is a protocol used to provide
security over the Internet. HTTPS prevents interceptions and interruptions
from occurring while the content is in transit.
For you to create a secure online connection, your website also needs an SSL
Certificate. If your website asks visitors to register, sign-up, or make a
transaction of any kind, you need to encrypt your connection.
What is SSL?
SSL (Secure Sockets Layer) is another necessary site protocol. This transfers
visitor’s personal information between the website and your database. SSL
encrypts information to prevent it from others reading it while in transit.
It denies those without proper authority the ability to access the data, as well.
GlobalSign is an example of an SSL certificate that works with most websites.
3.Choose a Smart Password
With there being so many websites, databases, and programs needing
passwords, it is hard to keep track. A lot of people end up using the same
password in all places, to remember their login information.
But this is a significant security mistake.
Create a unique password for every new log in request. Come up with
complicated, random, and difficult to guess passwords. Then, store them
outside the website directory.
For example, you might use a 14-digit mixture of letters and numbers as a
password. You could then store the password(s) in an offline file, a
smartphone, or a different computer.
Your CMS will request a login, and you must choose a smart password.
Refrain from using any personal information inside your password as well. Do
not use your birthday or pet’s name; make it completely unguessable.
After three months or sooner, change your password to another one, then
repeat. Smart passwords are long and should be at least twelve characters,
every time. Your password needs to be a combination of numbers and
symbols. Make sure to alternate between uppercase and lowercase letters.
Never use the same password twice or share it with others.
If you are a business owner or CMS manager, ensure all employees change
their passwords frequently.
4.Use a Secure Web Host
Think of your website’s domain name as a street address. Now, think of the
web host as the plot of “real estate” where your website exists online.
As you would research a plot of land to build a house, you need to examine
potential web hosts to find the right one for you.
Many hosts provide server security features that better protect your uploaded
website data. There are certain items to check for when choosing a host.
o Does the web host offer a Secure File Transfer Protocol (SFTP)?
SFTP.
o Is FTP Use by Unknown User disabled?
o Does it use a Rootkit Scanner?
o Does it offer file backup services?
o How well do they keep up to date on security upgrades?
Whether you choose SiteGround or WP Engine as your web host, make sure
it has what you need to keep your site secure.
5.Record User Access and Administrative Privileges
Initially, you may feel comfortable giving several high-level employees access
to your website. You provide each with administrative privileges thinking they
will use their site carefully. Although this is the ideal situation, it is not always
the case.
Unfortunately, employees do not think about website security when logging
into the CMS. Instead, their thoughts are on the task at hand.
If they make a mistake or overlook an issue, this can result in a significant
security issue.
It is vital to vet your employees before giving them website access. Find out if
they have experience using your CMS and if they know what to look for to
avoid a security breach.
Educate every CMS user about the importance of passwords and software
updates. Tell them all the ways they can help maintain the website’s safety.
To keep track of who has access to your CMS and their administrative
settings, make a record and update it often.
Employees come and go. One of the best ways to prevent security issues is
to have a physical record of who does what with your website.
Be sensible when it comes to user access.
6. Change Your CMS Default Settings
The most common attacks against websites are entirely automated. What
many attack bots rely on is for users to have their CMS settings on default.
After choosing your CMS, change your default settings immediately. Changes
help prevent a large number of attacks from occurring.
CMS settings can include adjusting control comments, user visibility, and
permissions.
A great example of a default setting change you should make is ‘file
permissions.’ You can change the permissions to specify who can do what to
a file.
Each file has three permissions and a number that represents every
permission:
o ‘Read ‘(4): View the file contents.
o ‘Write ‘(2): Change the file contents.
o ‘Execute ‘(1): Run the program file or script.
To clarify, if you want to allow many permissions, add the numbers together.
E.g., to allow read (4) and write (2), you set the user permission to 6.
Along with the default file permission settings, there are three user types:
o Owner – Often, the creator of the file, but ownership can be
changed. Only one user can be the owner at a time.
o Group – Each file is assigned to a group. Users who are part of
that specific group will gain access to the permissions of the
group.
o Public – Everyone else.
Customize users and their permission settings. Do not keep the default
settings as is, or you will run into website security issues at some point.
7. Backup Your Website
One of the best methods to keep your site safe is to have a good backup
solution. You should have more than one. Each is crucial to recovering your
website after a major security incident occurs.
There are several different solutions you can use to help recover damaged or
lost files.
Keep your website information off-site. Do not store your backups on the
same server as your website; they are as vulnerable to attacks too.
Choose to keep your website backup on a home computer or hard drive. Find
an off-site place to store your data and to protect it from hardware failures,
hacks, and viruses.
Another option is to back up your website in the cloud. It makes storing data
easy and allows access to information from anywhere.
Besides choosing where to backup your website, you must consider
automating them. Use a solution where you can schedule your site backups.
You also want to ensure your solution has a reliable recovery system.
Be redundant in your backup process — backup your backup.
By doing this, you can recover files from any point before the hack or virus
occurs.
8. Know Your Web Server Configuration Files
Get to know your web server configuration files. You can find them in the root
web directory. Web server configuration files permit you to administer server
rules. This includes directives to improve your website security.
There are different file types used with every server. Learn about the one you
use.
o Apache web servers use the .htaccess file
o Nginx servers use nginx.conf
o Microsoft IIS servers use web.config
Not every webmaster knows which web server they use. If you are one of
them, use a website scanner like Sitecheck to check your website. It scans for
known malware, viruses, blacklisting status, website errors, and more.
The more you know about the current state of your website security, the
better. It gives you time to fix it before any harm comes to it.
9. Apply for a Web Application Firewall
Make sure you apply for a web application firewall (WAF). It sets between
your website server and the data connection. The purpose is to read every bit
of data that passes through it to protect your site.
Today, most WAFs are cloud-based and are a plug-and-play service. The
cloud service is a gateway to all incoming traffic that blocks all hacking
attempts. It also filters out other types of unwanted traffic, like spammers and
malicious bots.
10.Tighten Network Security
When you think your website is secure, you need to analyze your network
security.
Employees who use office computers may inadvertently be creating an unsafe
pathway to your website.
To prevent them from giving access to your website’s server, consider doing
the following at your business:
o Have computer logins expire after a short period of inactivity.
o Make sure your system notifies users every three months of password
changes.
o Ensure all devices plugged into the network are scanned for malware
each time they are attached.
Why is Website Security Important?
Website security is important because nobody wants to have a hacked website. Having
a secure website is as vital to someone’s online presence as having a website host. If a
website is hacked and blocklisted, for example, it loses up to 98% of its traffic. Not
having a secure website can be as bad as not having a website at all or even worse. For
example, client data breach can result in lawsuits, heavy fines, and ruined reputation.
1 - Defense in Depth Strategy
A defense in depth strategy for website security looks at the depth of the defense and
at the breadth of the attack surface to analyze the tools used across the stack. This
approach provides a more accurate picture of today’s website security threat landscape.
2 -How Web Pros See Website Security
We can’t forget about the statistics, which make website security a compelling topic for
any online business—regardless of their size

What is website security?
Website security refers to the protection of personal and organizational public-facing
websites from cyberattacks.
Why should I care about website security?
Cyberattacks against public-facing websites—regardless of size—are common and may
result in:
• Website defacement,
• Loss of website availability or denial-of-service (DoS) condition,
• Compromise of sensitive customer or organizational data,
• An attacker taking control of the affected website, or
• Use of website as a staging point for watering hole attacks.
These threats affect all aspects of information security—confidentiality, integrity, and
availability—and can gravely damage the reputation of the website and its owner. For
example, organization and personal websites that fall victim to defacement, DoS, or data
breach may experience financial loss due to eroded user trust or a decrease in website
visitors.
What steps can my organization take to protect against
website attacks?
There are multiple steps organizations and security professionals should take to properly
secure their websites. Note: organizations should talk to their website hosting provider or
managed service provider to discuss roles and responsibilities for implementing security
measures.
1. Secure domain ecosystems.
• Review registrar and Domain Name System (DNS) records for all domains.
• Change all default password that were provided from your domain registrar and DNS.
o Default credentials are not secure—they are usually readily available on the
internet. Changing default usernames and passwords will prevent an attack that
leverages default credentials. (See Choosing and Protecting Passwords for
information on creating strong passwords.)
• Enforce multi-factor authentication (MFA). (See Supplementing Passwords for more
information)
• Monitor certificate transparency logs.
Review CISA Emergency Directive 19-01 and CISA Cyber Insights: Mitigate DNS
Infrastructure Tampering for more information.
2. Secure user accounts.
• Enforce MFA on all internet-accessible accounts—prioritizing those with privileged access.
• Implement the principle of least privilege and disable unnecessary accounts and
privileges.
• Change all default usernames and passwords.
Review CISA Cyber Insights: Enhance Email and Web Security for more information.
3. Continuously scan for—and remediate—critical and high vulnerabilities.
• Patch all critical and high vulnerabilities within 15 and 30 days, respectively, on internetaccessible systems. Be sure to scan for configuration vulnerabilities in addition to software
vulnerabilities.
o Enable automatic updates whenever possible.
• Replace unsupported operating systems, applications, and hardware.
Review CISA Emergency Directive 19-01 and CISA Cyber Insights: Remediate Vulnerabilities
for Internet-Accessible Systems for more information.
4. Secure data in transit.
• Disable Hypertext Transfer Protocol (HTTP); enforce Hypertext Transfer Protocol Secure
(HTTPS) and HTTP Strict Transport Security (HSTS).
o Website visitors expect their privacy to be protected. To ensure communications
between the website and user are encrypted, always enforce the use of HTTPS,
and enforce the use of HSTS where possible. For further information and guidance,
see the U.S. Chief Information Officer (CIO) and the Federal CIO Council’s webpage
on the HTTPS-Only Standard. Preload HSTS for all domains, when possible.
• Disable weak cyphers (SSLv2, SSlv3, 3DES, RC4).
Review CISA Binding Operational Directive 18-01 and CISA Cyber Insights: Enhance Email
and Web Security for more information.
5. Backup data.
• Employ a backup solution that automatically and continuously backs up critical data and
system configurations from your website.
• Keep your backup media in a safe and physically remote environment.
• Test disaster recovery scenarios.
6. Secure web applications.
• Identify and remediate the top 10 most critical web application security risks; then move
on to other less critical vulnerabilities. (Refer to OWASP Top 10 for a list of the most critical
web application security risks.)
• Enable logging and regularly audit website logs to detect security events or improper
access.
o Send the logs to a centralized log server.
• Implement MFA for user logins to web applications and the underlying website
infrastructure.
7. Secure web servers.
• Use security checklists.
o Audit and harden configurations based on security checklists specific to each
application (e.g., Apache, MySQL) on the system.
• Use application allow listing and disable modules or features that provide capabilities that
are not necessary for business needs.
• Implement network segmentation and segregation.
o Network segmentation and segregation makes it more difficult for attackers to
move laterally within connected networks. For example, placing the web server in
a properly configured demilitarized zone (DMZ) limits the type of network traffic
permitted between systems in the DMZ and systems in the internal corporate
network.
• Know where your assets are.
o You must know where your assets are in order to protect them. For example, if you
have data that does not need to be on the web server, remove it to protect it from
public access.
What are some additional steps to protect against website attacks?
• Sanitize all user input. Sanitize user input, such as special characters and null characters,
at both the client end and the server end. Sanitizing user input is especially critical when it
is incorporated into scripts or structured query language statements.
• Increase resource availability.
Configure website caching to optimize resource
availability. Optimizing a website’s resource availability increases the chance that it will
withstand unexpectedly high amounts of traffic during DoS attacks.
• Implement cross-site scripting (XSS) and cross-site request forgery (XSRF)
protections. Protect website systems, as well as website visitors, by implementing XSS
and XSRF protections.
• Implement a Content Security Policy (CSP).
Website owners should also consider
implementing a CSP. Implementing a CSP lessens the chances of an attacker successfully
loading and running malicious JavaScript on the end user machine.
• Audit third-party code.
Audit third-party services (e.g., ads, analytics) to validate that no
unexpected code is being delivered to the end user. Website owners should weigh the pros
and cons of vetting the third-party code and hosting it on the web server (as opposed to
loading the code from the third party).
• Implement additional security measures.
Additional measures include:
o Running static and dynamic security scans against the website code and system,
o Deploying web application firewalls,
o Leveraging content delivery networks to protect against malicious web traffic, and
o Providing load balancing and resilience against high amounts of traffic.
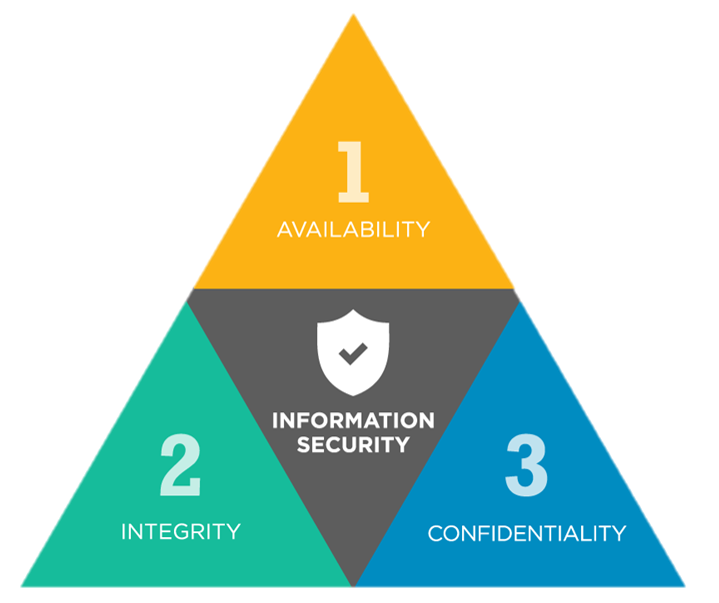
Information Security CIA Triad
A benchmark in information security is the CIA triad – Confidentiality, Integrity and
Availability. This model is used to develop policies for securing organizations.
1. Confidentiality
Confidentiality refers to access control of information to ensure that those who should
not have access are kept out. This can be done with passwords, usernames, and other
access control components.
2 . Integrity
Integrity ensures that the information end-users receive is accurate and unaltered by
anyone other than the site owner. This is often done with encryption, such as Secure
Socket Layer (SSL) certificates which ensure that data in transit is encrypted.
3. Availability
Availability rounds out the triad and ensures information can be accessed when
needed. The most common threat to website availability is a Distributed Denial of
Service attack or DDoS attack